wRITING ON THE EDGE
As some of you already know, I am currently enrolled in a graduate program at New York University to earn my master's degree in cybersecurity. This was my first semester, and, for one of my classes, I was assigned a research project. Since it's best practice in the science community to make research available for peer review, I figured I'd share my extended abstract with my favorite readers of all time: you! Please feel free to email me to share your feedback as well as to offer insights into other problem domains.
Abstract
Data generation and consumption has exploded since the internet was first introduced to the public almost 30 years ago. While this makes things, such as shopping, paying bills, and remote work/school more accessible, it also creates challenges in other areas, like the justice system in particular. As the digital transformation continues to proliferate, the law enforcement relies more and more on digital forensics when investigating criminal cases. Several researchers have proposed frameworks to guide digital forensics investigations; however, none have eliminated the line between criminal investigations and digital forensics investigations. This paper presents an abstract framework for the preservation, collection, validation, identification, analysis, interpretation, documentation, and presentation of digital evidence as a branch of the criminal investigation process.
I. INTRODUCTION
In the second edition of [1], Casey describes technology as a window into our lives and the lives of criminals. However, in his current, third edition, he points out the metaphor no longer applies, that the separation between virtual and physical worlds that once existed is now gone.
Despite this, the most prevalent digital forensics investigations models available today still provide a framework that is separate from the overall criminal investigation process. Because technology has become integrated into almost every aspect of our daily lives, every violent crime should include digital evidence [1]. I would argue that this claim need not be limited to violent crimes but apply to all crimes in general.
One of the major hurdles when it comes to digital forensics is the constant rate of change in technology [2]. This not only makes it difficult for law enforcement, forensic experts, and the courts to develop standardized procedures for active investigations but also for maintaining the accuracy and trustworthiness of digital evidence stored after being heard in court for reexamination in case of an appeal or maybe indefinitely for cases that have gone cold [2].
Data contained on personal devices, such as cellphones, laptops, tablets, navigation systems, etc., can provide several clues that allow for a more complete recreation of events. By including digital evidence as a part of all criminal investigations, the standards and procedures can evolve in ways that keep pace with advancements in technology, and there won’t be as much disparity between law enforcement, digital forensic practitioners, lawyers, and judges.
Using threat modeling, I identified the vulnerabilities that exist in the current frameworks and use this evidence to propose an abstract framework that would mitigate these risks.
The organization of the paper is as follows. Section II includes related research and how it differs from my proposal. In Section III, I share a motivating example. I’ll present my hypothesis along with the empirical evidence in Section IV. I conclude the findings of my research in Section V and discuss future work.
II. RELATED RESEARCH
In Reith et. Al. [3], they build off other available models to develop a framework that is not technology specific and can therefore be used for both current and future devices. The reason this doesn’t work is that it’s too specific in some areas and too generic in others. For example, it focuses only on cybercrimes and it does not list any sub-steps.
Ieong [4] attempts to break the technical barrier between information technologists, legal practitioners, investigators, and their corresponding tasks together with a technical-independent framework. While the framework should bring together all parties involved in criminal investigations, the technical aspect is necessary for the digital element, and, so, the FORZA model is incomplete.
The framework proposed in [5] builds on existing frameworks and includes all of the higher-order, single-tier approaches that exist in the various models. But, it goes on to add objectives-based sub-phases. The authors themselves point out the proposed model is incomplete and was initially designed only for mainstream computer and network forensics with the goal of stimulating additional conversation and development for a complete digital forensics investigation framework.
III. MOTIVATING EXAMPLE
The Innocence Project is a nonprofit organization that exonerates wrongly convicted individuals and promotes the reformation of the criminal justice system to prevent similar cases of injustice from occurring in the future [3]. The misapplication of forensic science contributed to 52% of wrongful convictions in Innocence Project cases. False or misleading forensic evidence was a contributing factor in 24% of all wrongful convictions nationally, according to the National Registry of Exonerations, which tracks both DNA and non-DNA based exonerations [4].
IV. HYPOTHESIS & EVIDENCE
Based on the models presented in the related research section of this paper, I hypothesized that none of them would achieve an overall low score on a risk assessment using the STRIDE method to identify risks and the DREAD rating system to qualitatively rank them. A total of 21 threats were identified – 4 spoofing, 3 tampering, 7 repudiation, 1 information disclosure, 5 denial of service, and 1 elevation. Each STRIDE category was given its own DREAD ranking, and a total score was calculated at the end. Since the DREAD ranking system classifies a score of 5-7 as low, 8-11 as medium, and 12-15 as high, my metric used 105-147 as low, 168-231 as medium, and 252-315 as high (DREAD scores multiplied by 21). The results are shown below in Table 1.
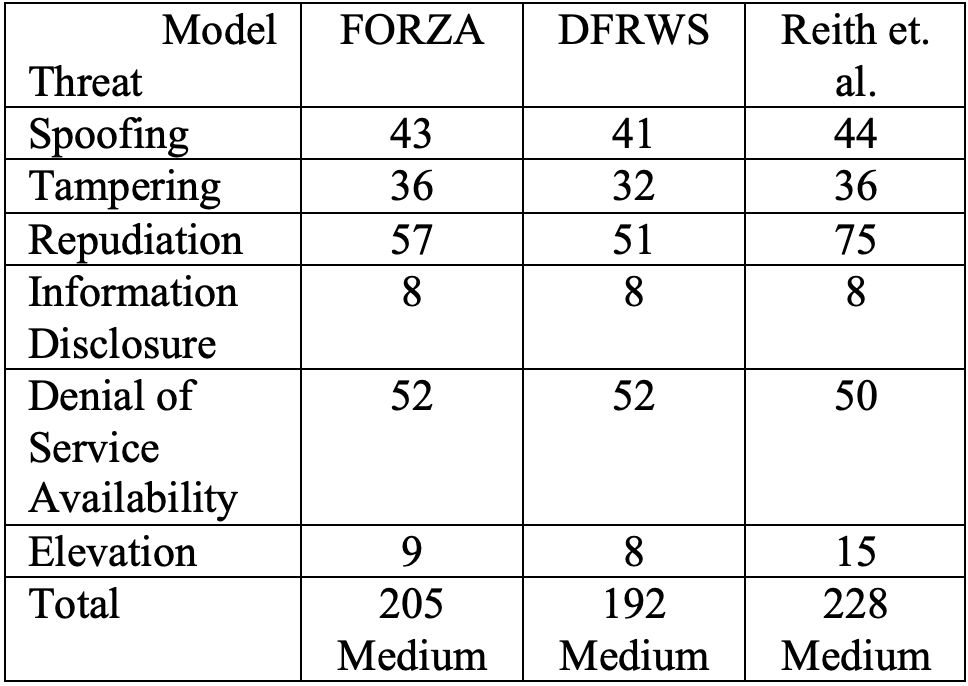
Table 1 compares three digital forensics frameworks using the STRIDE method to identify threats and the DREAD system to rank them.
V. CONSLUSION AND FUTURE WORK
Based on the risk assessment, my original hypothesis was correct. While some of the models were better in some areas than others, they are all lacking in providing a complete digital forensics investigation framework that maintains the accuracy and integrity of digital evidence in criminal investigations.
Future work of this project should include a risk assessment with several parties involved, including but not limited to law enforcement from various geographical areas, lawyers, judges, lawmakers, cybersecurity experts, and the general public. This should be done with a series of groups, so the results can be combined to provide a more thorough assessment. Once this is complete, careful consideration should be given to each threat in order to create a framework that minimizes the risks identified. Furthermore, a framework to minimize damage should also be developed in the event that attacks do occur because it’s more likely they will than they won’t.
The most critical threat based on my findings is that digital evidence is still considered separate from criminal investigations that do not involve cybercrimes. Therefore, valuable digital evidence is often overlooked in the beginning, which means it can be damaged, altered, or destroyed in the meantime. Including digital evidence in every criminal investigation and training all parties involved on the preservation, collection, validation, identification, analysis, interpretation, documentation, and presentation of digital evidence is crucial to preventing future injustice.
VI. REFERENCES
[1] E. Casey, Digital Evidence and Computer Crime, Baltimore: Elsevier Inc., 2011.
[2] A. Jansen, "Digital Records Forensics: Ensuring Authenticity and Trustworthiness of Evidence Over Time," in International Worksho¬p on Systematic Approaches to Digital Forensic Engineering, Vancouver, 2010.
[3] M. Reith, C. Carr and G. Gunsch, "An Examination of Digital Forensic Models," International Journal of Digital Evidence, vol. 1, no. 3, p. 12, 2002.
[4] R. S. Ieong, "FORZA - Digital forensics investigation framework that incorporate legal issues," Digital Investigation, vol. 3S, pp. 29-36, 2006.
[5] N. L. Beebe and J. G. Clark, "A hierarchical, Objectives-Based Framework for the Digital Investigations Process," in The Digital Forensic Research Conference, Baltimore, 2004.
[6] The Innocence Project, "The Innocence Project - About," MADEO, 2021. [Online]. Available: https://innocenceproject.org/about/. [Accessed 2 December 2021].
[7] The Innocence Project, "The Innocence Project - Overturning Wrongful Convictions Involving Misapplied Forensics," MADEO, 2021. [Online]. Available: https://innocenceproject.org/overturning-wrongful-convictions-involving-flawed-forensics/. [Accessed 2 December 2021].
Amy Al-Katib
Amy Al-Katib, CDCDP, is editor-in-chief of Mission Critical magazine. She is a member of 7x24 Exchange Intl., ASIS Intl., BICSI, iMasons, the International Society of Philosophical Enquiry, and Mensa. She holds a bachelor’s degree in journalism from Michigan State University and a certificate in STEM/computer science from New York University. She is currently enrolled in the Master's of Science Cybersecurity program at NYU. Reach her at al-katiba@bnpmedia.com.

